- The High-Level Flow of a Credit Card Payment
- Payment Submission: The Starting Line
- Authorization: Payments Data on the Move
- Authentication: Making Sure Everything Is on the Up and Up
- Clearing: Getting the Money Moving
- Settlement: Money in the Bank
- A Complex Journey We All Take for Granted
You click the pay button. A second or two later, you get an order confirmation. You’re done. Success! That’s how most consumers think about credit card payments — which is to say, they don’t really think about them at all. Whether they’re making an in-store, online, unattended or embedded payment, what’s going on behind the curtain is irrelevant, as long as it’s easy and it works.
For merchant services providers, it’s different. Independent sales organizations (ISOs) and payment facilitators (PayFacs) are more involved in the payment process. In contrast, independent software vendors (ISVs) typically partner with providers and take a back seat.
For instance, most software companies won’t have to handle any of the nitty-gritty back-end processes, while ISOs and PayFacs juggle various levels of involvement.
However, whether you’re a software provider or a new ISO or PayFac, once you start offering payment acceptance to your customers, it’s crucial to understand what’s going on in those two seconds between an end customer clicking pay and seeing the order confirmation screen.
In this guide, we’ll take you on the same journey that a customer’s card information, personal data and funds go on every time they make a purchase. By the end, you’ll have a working knowledge of how credit card payments work and how to improve the buying experience for your customers.
The High-Level Flow of a Credit Card Payment
We’ll start with a high-level overview of what happens during processing and go into more detail as we progress through the journey.
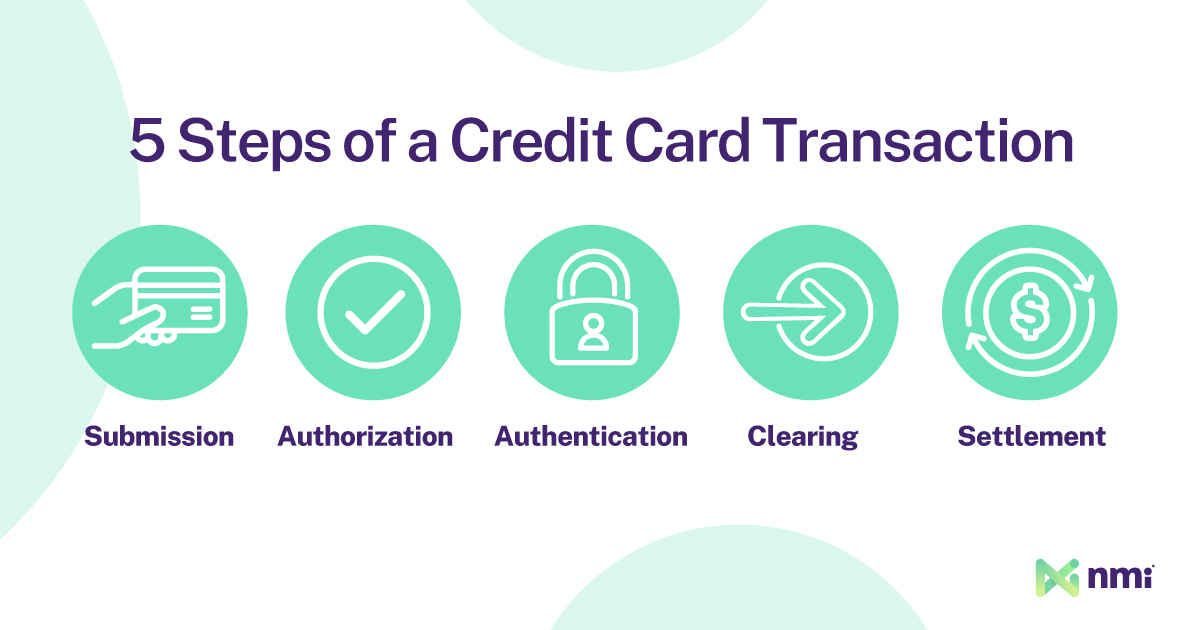
The general path every credit card transaction goes through involves five steps: submission, authorization, authentication, clearing and settlement.
- Submission: In the submission stage, the cardholder makes the payment by tapping, swiping, inserting or entering their card details. Security starts at this stage, and there is more going on than meets the eye.
- Authorization: Next, the payment must be authorized. In this stage, the data from the payment goes to no less than three separate parties. Ultimately, the bank that issued the customer’s credit card decides to approve or decline the transaction.
- Authentication: Before a payment is approved and authorized, the transaction must also be authenticated. During authentication, the merchant and the customer’s banks verify that the card and purchase details match what’s expected and don’t trigger any fraud warnings. The bank then checks for available funds. If everything looks good, an approval is sent back across the network. The funds are put on hold, and the merchant gets the OK to release the goods or services. This is the end of the two seconds between tap and beep, but it isn’t the end of the journey.
- Clearing: During the clearing stage, merchants will send their recent transactions to their processor or bank in one big batch — a term we’ll explain later. The processor then sends the batched transactions to the card network, and the card network disperses them to the various banks of the customers who made the purchases.
- Settlement: In the final stage, the customers’ banks send the money to the card network (minus some fees). From there, it is forwarded to the merchants’ banks (minus some more fees) before being dispersed into the merchants’ bank accounts. This process is known as settlement or funding.
That’s the abbreviated version of how credit card payments and customer data move from place to place. Yet, there is much more to it.
Payment Submission: The Starting Line
When a consumer submits a card payment online or at a physical terminal, the unsung hero of the interaction is the payment gateway.
The payment gateway is the software that captures and transmits the sensitive data from a customer’s card (along with other key transaction information) to the acquirer so the authorization process can happen. For online and software-based payments, the gateway runs in the background behind the checkout page. In-store, the gateway software is built into the merchant’s physical payment hardware.
In addition to facilitating the flow of data to and from the merchant, the payment gateway is also the first line of defense against bad actors looking to steal valuable customer data.
Several initial security measures begin at the gateway level. The first and most universal is encryption. All gateways encrypt customer payment data before sending it. At the most basic level, they use legacy protocols like SSL (Secure Sockets Layer) and TLS (Transport Layer Security). However, modern gateways increasingly employ a more advanced and secure method known as tokenization.
A gateway can also require additional security steps that must be met before submission, like 3DSecure or the European Union’s Strong Customer Authentication (SCA). The former requires online shoppers to enter a PIN before a transaction can go through. This step ensures an authorized holder is using the card.
Authorization: Payments Data on the Move
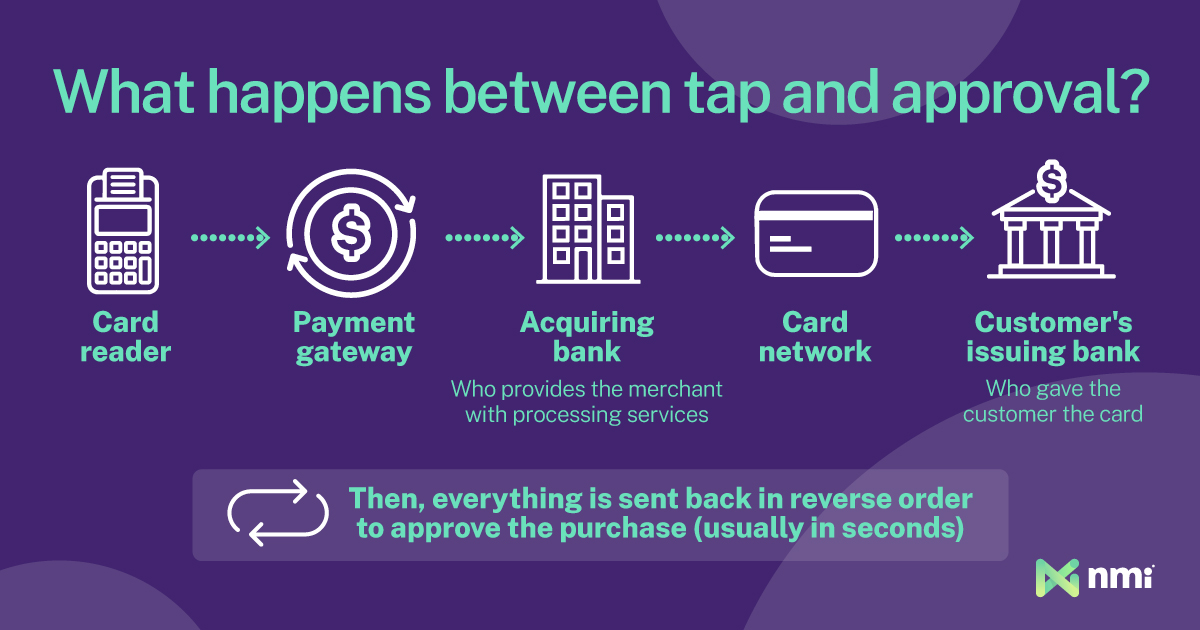
With the customer’s data secured, the payment gateway sends all relevant information to the next party. The data will go to three recipients: the merchant’s acquiring bank, the affiliated credit card network and the customer’s issuing bank.
The first stop is the acquiring bank, which provides the merchant with credit card processing services. The acquiring bank is the only point of contact for the merchant. As such, all transactions must go through it first.
Next, the acquiring bank forwards the data to the affiliated credit card network. This is the network whose brand is on the card: Visa, Mastercard, Discover, etc. The major card networks act as intermediaries between their various partner banks; they set and enforce the rules and act as the central hub for payment authorizations. After this step, the card network forwards the authorization requests from the merchant’s acquiring bank to the customer’s card-issuing bank.
The issuing bank is the one that gave the customer the credit card. The card may have Visa or Mastercard branding, but it’s the bank featured on the card that does the heavy lifting. The issuing bank is the final outbound stop for the customer’s payment data. For most transactions, the issuing bank will receive these key details:
- The card number
- The card’s expiration date
- The holder’s name and address
- The card’s CVV security code
- The purchase amount
It’s worth noting that the actual data captured and sent at the time of submission can vary depending on the purchase type. Some high-value transactions like the ones commonly made in large business-to-business (B2B) and business-to-government (B2G) sales — known as Level 2 or Level 3 transactions — require significantly more information.
Authentication: Making Sure Everything Is on the Up and Up
Approval of the payment authorization request falls on the issuing bank since it’s the party extending the credit. Before an authorization can go through, the request must be authenticated.
The authentication process ensures the transaction is legitimate and the cardholder is who they say they are. In the past, authentication was purely the merchant’s responsibility, and asking for a signature or a piece of ID was the most security they performed. Today, authentication is high-tech and highly automated. It happens both on the merchant’s end and at the issuing bank.
Numerous tools are available to help merchants with authentication, especially for card-not-present ecommerce and embedded payments. For instance, the address verification system (AVS) can check a customer’s entered address to ensure it matches the one on record with the bank.
Additionally, AI-powered third-party fraud prevention tools, like Kount, can compare transaction data to a huge anti-fraud database built from billions of transactions. Merchants can also use preset rules to flag potentially suspicious transactions for manual review or outright denial, all before the data begins its journey.
An additional risk assessment happens once the payment data reaches the issuing bank. Assuming everything looks good, the final step of the authorization and authentication processes is to check for available credit and approve or deny the transaction.
The authorization or denial is sent back across the network in the reverse order: from the issuing bank, through the card network, to the acquiring bank and back to the merchant and customer through the payment gateway. This entire process, from submission to approval and purchase confirmation, occurs automatically, often in seconds. Approval, however, is not the end of the process — at least not for the merchant and the banks.
Clearing: Getting the Money Moving
The first three processes let the merchant know if a transaction can proceed. At this stage, no money has changed hands (yet). Funds begin their movement during an entirely separate process, beginning when the merchant submits the accepted transaction for clearance.
Clearing involves all three behind-the-scenes parties — the acquiring bank, the card network and the issuing bank.
The clearing process begins with batching. Merchants don’t send new transactions in to be cleared one at a time. Instead, they lump transactions together to submit in large batches. Each batch submission incurs a fee, so most merchants batch and submit once per day after closing. Large merchants doing high volumes will often batch twice or more each day.
Merchants send batches to their acquiring bank or the payment processors they work with. A batch could contain hundreds or thousands of card transactions, all of which must arrive at the correct issuing banks to be settled. To facilitate that complex task, the acquirer sends the batch off to the card network, which sorts the transactions and routes each to the bank that issued the card used to pay for the final settlement.
Settlement: Money in the Bank
Once clearing is complete, the issuing bank deducts the amount from the cardholder’s available credit and sends it to the card network, again acting as an intermediary. The credit network forwards the funds to the acquirer, who deposits funds into the seller’s merchant account — a process known as funding or settlement.
Unlike the authorization process, which takes seconds from start to finish, clearing and funding generally take longer — often two to three business days. As a result, there is usually a delay between when a merchant makes a non-cash sale and when they have access to the money from it.
That delay, known in the industry as a standard hold, is another safety mechanism. It provides a buffer that gives the entire system extra time to shake out fraud and safeguard liquidity.
While a two-day delay is standard, many acquirers and payment processors offer next-day and same-day funding services to help attract merchants in an increasingly competitive payments market. However, these services don’t reduce or eliminate the delay in the process. Instead, they extend brief credit to the merchant, providing them with the necessary funds until the settlement is complete.
A Complex Journey We All Take for Granted
While ISOs and PayFacs are more involved in the process, for software vendors, everything happens in the background. However, when you dig into it in detail, it’s hard not to appreciate the intricacies that go into processing 1.86 billion credit card transactions per day.
At NMI, we’re committed to ensuring your merchants keep taking that process for granted by enabling you to offer them the most frictionless, affordable and transparent payments possible. From processing to gateways to merchant relationship management and beyond, our fully modular embedded payments allow you to build the ideal solution to serve your users and maximize payment earnings.
To learn more about NMI’s turnkey modular payment solutions, reach out to a member of our team and schedule a consultation.
Don’t just turn on payments, transform the way you do business
- Generate New Revenue By adding or expanding payment offerings to your solution, you can start earning higher monthly and transaction-based recurring revenue.
- Offer the Power of Choice Allow merchants to choose from 125+ shopping cart integrations and 200+ processor options to streamline their onboarding.
- Seamless White Labeling Make the platform an extension of your brand by adding your logo, colors and customizing your URL.





